You Are Exposed to Critical Risks
Critical Risks are exposed to your People, your Processes, and your Technology. These threads are interwoven, and they may be manipulated or exploited by hackers creating Unidentified Critical Risks that can result in Cascading Failures. Managing the interdependencies and measuring the impacts is fundamental to a mature cybersecurity program.
Unidentified Critical Risks
- Customer Data Exploited
- Failure of Devices Leading to Key Production Process Disruption
- Service Delivery Interruptions
- Core Intellectual Property Compromised
- Supply Chain Compromises Leading to Service Failure
Failure Examples
- Colonial Pipeline (2021)
Hackers gained access to the network using a key VPN legacy system. Compromise of internal devices led the company to shutting down pipeline operations across the east coast. - JBS (2021)
Hackers gained access to the meat processor’s network leading to the disruption of cattle processing operations in plants across three countries. - City of Baltimore (2019)
Cyber criminals gained access to several points in the city’s network shutting down a variety of key services including water billing services, titling operations, and parking tickets and fines.
Reveal and Resolve
A hacker tests each thread, finding vulnerabilities, to fray the fabric of your organization. With thousands of devices and vulnerabilities, where do you start? By mapping and assessing your most critical operational elements, you can better plan your defensive strategies. DPA’s expert tools and guidance help you create a integrated plan to leverage your existing cybersecurity tools so you can be prepared, resistant, and resilient to potential cyber threats.
Developed and backed by University of Maryland research, our award-winning TAPESTRY solution helps you understand how each of your organizational threads are interwoven and interdependent. Guided by the expertise of DPA, you will gain insight into the complexities of your organizational processes and their vulnerabilities, to help you better allocate resources, promote security, stability, and success.
Testimonial
Protected Clients





Proven Expertise and Results
You Can Rely On
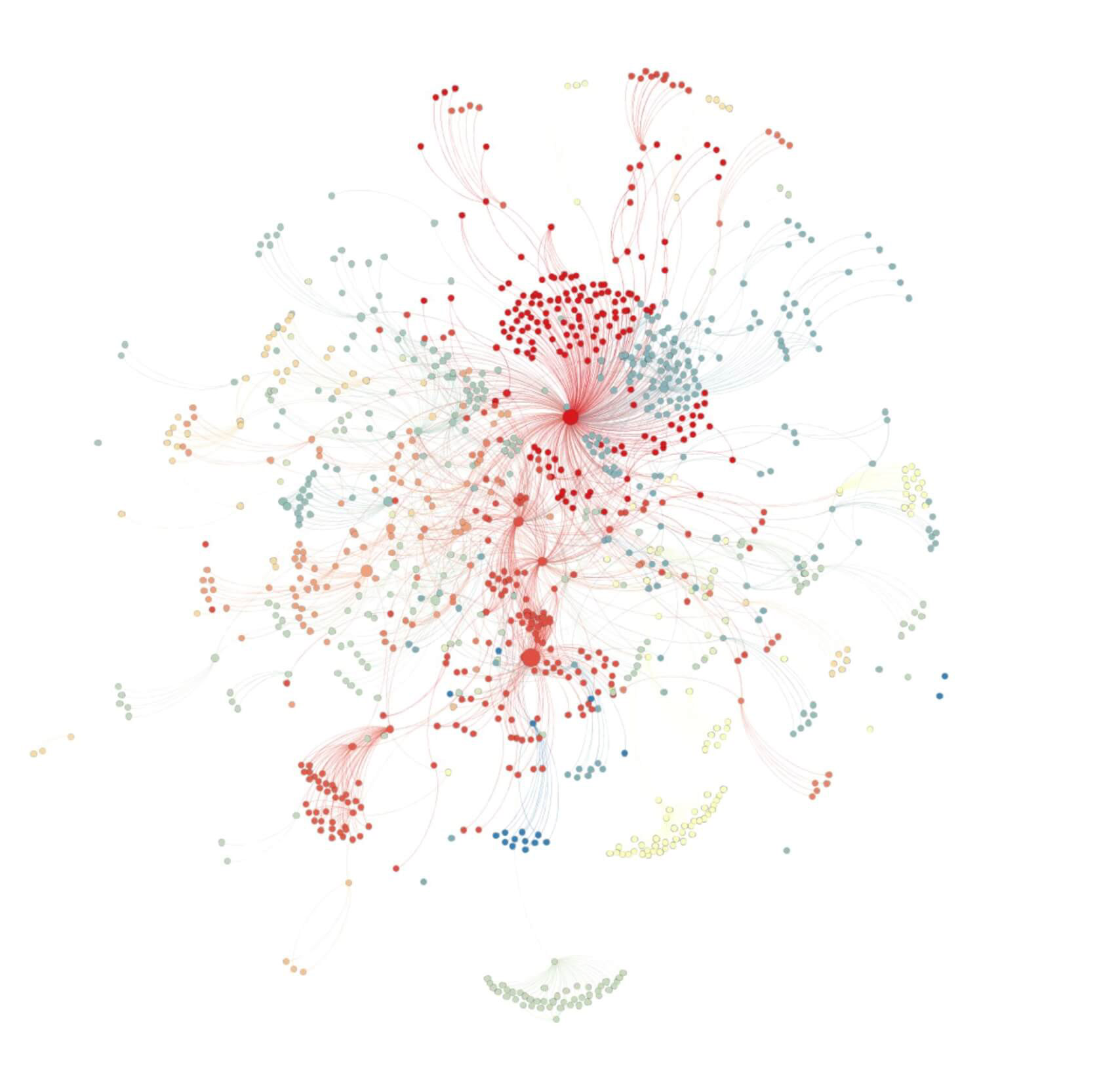
Decision Point Analytics (DPA) provides a managed approach to quantifying cyber risk and maturity in your organization. Key to managing cyber risk is the ability to effectively measure the strategic effect a cyber-attack has on the series of interconnected infrastructures that can generate substantial impacts on your organization. We do so by utilizing our groundbreaking application TAPESTRY, and leverage decades of experience in the intelligence community, private industry, and academia to help you identify optimal areas to invest your security dollar.
Based on award winning university research, TAPESTRY, guides your decision-making process, providing insight and recommendations to help you allocate resources to reduce interconnected risks throughout your organization. Our approach meets NIST and ISO standards by generating a repeatable and scaled approach for measuring and reducing cyber risks through all levels of your organization. DPA is a preferred partner for providing ISACA’s CMMI diagnostic software solution and is a trusted partner for customers in the private and public sector.
